-
首页
-
Industrial control safety
Introduction to industrial control safety
Cloud series products
Industrial monitoring and situational awareness platform
Net series products
Centralized safety management system
Industrial safety isolation network gate system
Industrial safety audit system
Industrial control honeypot system
Industrial asset exploration and full life cycle management system
End series product
UHC Security Audit protection system
The host security hardening system
Industrial network security terminal gateway system
Inspection series
Industrial Safety assessment System
Industrial Control Safety Information Center
Vulnerability information base
New service of industrial control safety
Industrial control safety risk assessment services
Industrial control assets sorting and full life cycle management services
Industrial control security penetration services
Industrial control safety active defense services
Industrial control security border protection services
Industrial control safety operation services
Training actual combat parallel simulation laboratory construction services
-
Offensive and defensive security
-
Data security
-
Operation and maintenance + Security
-
Safe operation
Introduction to safe operation
Product series
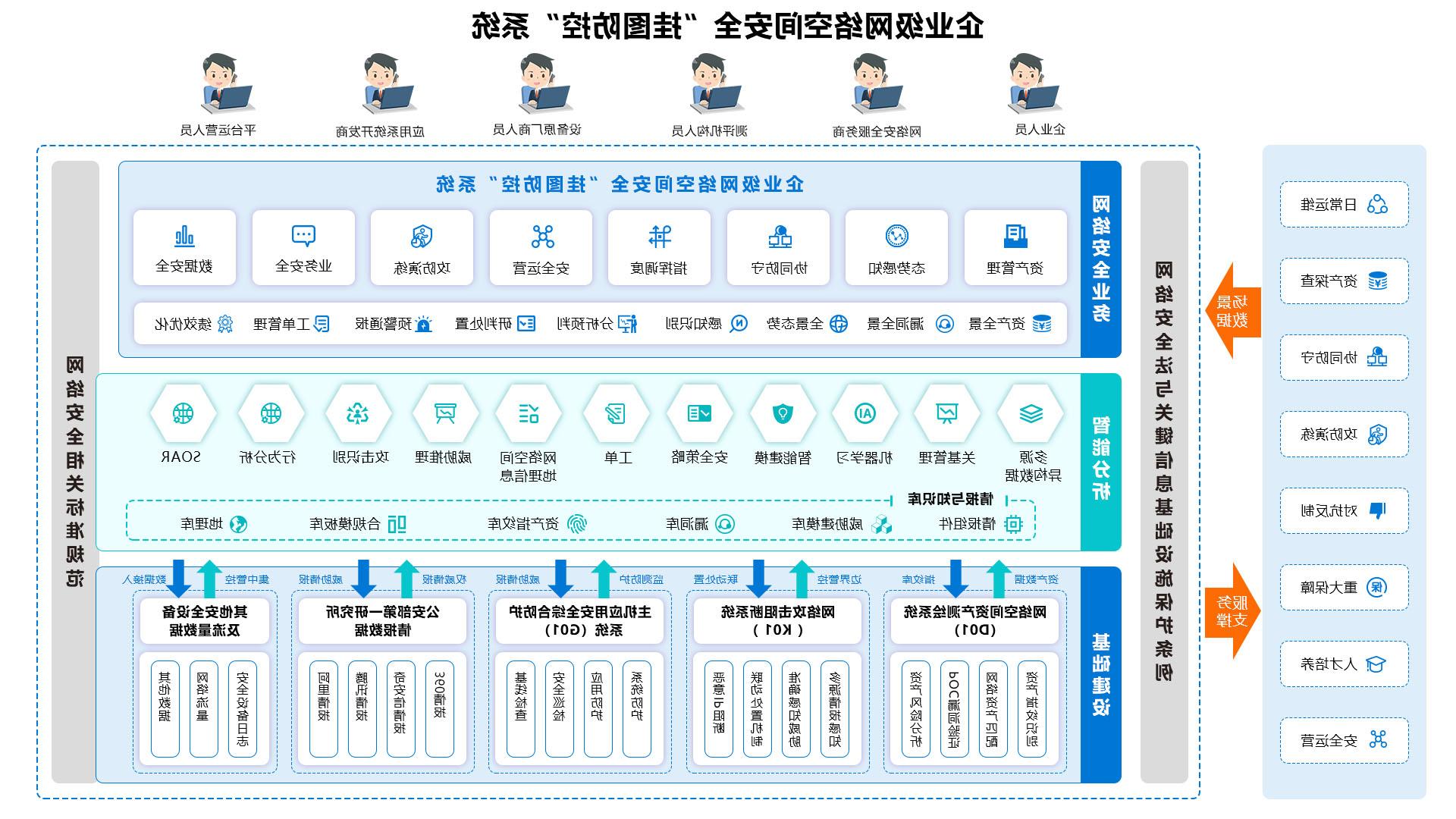
Cyberspace security wall chart prevention and control platform
Website cloud protection platform
Fishing drill service platform
Application host Integrated protection system G01
Network asset mapping analysis system D01
Internet exposure asset risk dynamic monitoring system FD01
Network violation external audit system E01
Network attack blocking system K01
Security service
Safe community
-
Education and training
-
Industry program
-
Into the sky










 Yuntian security subscription number
Yuntian security subscription number
 Cloud Sky Security Service number
Cloud Sky Security Service number
